Spyware is a prevalent threat in the digital world, characterized as a type of malicious software that covertly infiltrates computing devices to gather personal and sensitive data without the user’s consent. It is proficient at monitoring online activities, logging keystrokes, accessing confidential files, and potentially hijacking webcams. This harmful software commonly enters systems through deceptive methods such as phishing emails, compromised websites, or being hidden within legitimate software downloads. Once installed, spyware is notoriously challenging to detect and remove, often requiring specialized tools and expertise. It is crucial for individuals and organizations to have a thorough understanding of spyware, its various forms, and the associated risks in order to establish effective defenses and safeguard against potential consequences such as identity theft, financial fraud, and privacy breaches.
Specification Table of Spyware
| Specification | Details |
| Name | Varies (e.g., CoolWebSearch, Gator, Zlob, etc.) |
| Type | Malware |
| Category | Spyware |
| Primary Objective | To gather information about an individual or organization without their knowledge or consent |
| Common Infection Methods | Phishing emails, malicious websites, software bundles, exploits |
| Targeted Data | Keystrokes, browsing history, system information, confidential documents |
| Stealth Mechanisms | Hides from users, masquerades as legitimate software, disables security measures |
| Communication | May use encrypted channels to communicate with a command and control server |
| Persistence | Often includes mechanisms to remain on the system after reboot or attempts to remove it |
| Impact | Privacy invasion, data theft, potential financial loss, identity theft |
| Detection | Anti-spyware software, antivirus programs, network monitoring tools |
| Removal | Specialized removal tools, antivirus software, manual removal by experts |
| Prevention | Regular software updates, user education, reputable antivirus/anti-spyware software |
| Legal Status | Illegal in many jurisdictions without the target’s consent |
| Notable Examples | Pegasus, DarkHotel, FinFisher |
| Targeted Devices | Both personal and corporate devices, including computers, smartphones, and tablets. |
History of spyware
Spyware, a term that originated in the early 1990s, refers to malicious software that infiltrates devices to monitor user behavior, harvest personal data, and transmit this information to third parties, often for advertising purposes. Its proliferation coincided with the growth of the World Wide Web, reaching its peak threat to privacy and system integrity in the early 2000s. The US’s Spy Act of 2005 is one legislative effort to combat spyware by penalizing unauthorized data collection. Despite the development of anti-spyware tools, the battle against these clandestine programs continues as they become more sophisticated. The term gained public attention in 1995 and by the late 1990s, it was widely recognized as a form of malware. The first anti-spyware program, Opt Out, was developed by Steve Gibson in 1999 after he discovered software covertly collecting data on his system. By the early 2000s, the issue had escalated, with studies showing a majority of internet-connected computers infected, leading to increased awareness and the creation of tools to safeguard user privacy and improve system performance.
Types of Spyware (DND)
Spyware is a form of malicious software that infiltrates computing devices in order to collect sensitive information without the user’s permission, presenting substantial privacy and security threats. It can appear in different variations, each created to observe, pilfer, and transmit personal data to unauthorized third parties. Recognizing the various forms of spyware is essential for identifying potential risks and establishing successful protective measures. In this article, we examine the main categories of spyware that users should be familiar with in order to enhance the security of their digital environments.
- Adware
- Trojans Horse Virus
- System monitors
- Tracking cookies
- Keyloggers
- Infostealer
- Rootkits
- Red Shell
- System monitors
- Browser hijackers
- Web beacons
- Password theft spyware
- Modem hijacker
- Mobile spyware or stalkerware
- Cookie trackers
What Does Spyware Do?
From keystrokes to browsing habits, spyware discreetly gathers data, presenting substantial risks to privacy and security. The following are the main actions spyware can perform once it has infected a device:

1. Infiltrate
Spyware is a type of malicious software that covertly infiltrates a user’s device in order to monitor and collect sensitive data, such as keystrokes, browsing habits, and login credentials, often without the user’s knowledge or consent. It typically gains entry through deceptive methods such as bundled software, apps, media files from untrustworthy sources, phishing emails, or by exploiting security vulnerabilities. Once installed on the system, spyware remains hidden to evade detection by antivirus programs, allowing it to carry out harmful activities that jeopardize privacy and security. The information gathered by spyware can be used for malicious purposes, including identity theft, financial scams, and targeted advertising, making spyware a powerful tool for cyber espionage and the misuse of personal data.
2. Monitor and capture data
The monitoring and capturing of a wide range of personal data without user consent is a serious issue. Once installed in a system, this software operates discreetly in the background, tracking internet activity, recording keystrokes, and collecting sensitive information such as login details, financial data, and private messages. This covert behavior can lead to breaches of privacy, identity theft, and significant security risks. In addition to data theft, spyware can alter system configurations, reduce performance, and undermine user control, all while avoiding detection to ensure its persistence. The continuous transmission of stolen data to remote servers poses a significant threat to individual privacy and organizational security, as well as creating opportunities for additional security vulnerabilities.
3. Send or sell stolen data
Spyware is a form of malicious software that secretly infiltrates computer systems in order to monitor and steal sensitive information, such as personal and financial data, login credentials, and confidential communications. It operates discreetly by tracking activities, recording keystrokes, and accessing private documents, before transmitting or selling the stolen data to third parties like cybercriminals or data traffickers. The consequences of these actions can be significant, potentially resulting in identity theft, financial harm, and serious breaches of privacy. The sharing of this information with interested parties can greatly compromise both individual and corporate digital security, underscoring the importance of understanding spyware to proactively defend against such exploitation in the digital realm.
How Does Spyware Work?
Spyware functions by surreptitiously infiltrating your device, frequently without your awareness or permission. It subsequently observes your actions, gathers sensitive data, and is capable of altering your device’s operations. Here is a more detailed examination of how spyware operates:
1. Infection
Spyware infections typically begin when a user unknowingly interacts with a malicious source such as a deceptive link, compromised software download, or infected email attachment. The spyware then covertly infiltrates the system, often disguising itself as legitimate software or attaching to authentic applications to avoid detection. By exploiting vulnerabilities in the system or applications, the spyware can gain unauthorized access and make changes to system settings, monitor user activity, and transmit collected data, including passwords, financial information, and personal communications, to a remote attacker. The main danger of spyware lies in its secretive nature, as it silently gathers sensitive user information without permission, posing a serious threat to privacy and potentially causing financial or reputational harm.
2. Concealment
Spyware operates with a high level of deception, often disguising itself as legitimate software to infiltrate systems undetected and embedding itself deeply within device processes. It employs sophisticated concealment tactics, including rootkit technology to manipulate low-level system functions and evasion of standard interfaces, to remain hidden. By doing so, it can silently monitor and record a wide range of user activities, from keystrokes to browsing habits, and stealthily harvest personal and financial data. Advanced spyware can even neutralize anti-virus tools by disabling them or encrypting its code to escape detection. This allows it to persist on a device, continuously breaching user privacy and posing serious security threats without the user’s awareness or ability to easily remove it.
3. Data Collection
The primary function of the system is data collection, achieved through covert monitoring and recording of user activities. It utilizes keyloggers to capture keystrokes, allowing access to sensitive information such as passwords and credit card numbers. In addition, spyware monitors browsing habits and collects personal data from online forms and cookies. Advanced versions of the spyware can take screenshots, activate cameras, and record personal interactions and surroundings using microphones. The collected data is then transmitted to remote servers in a secretive manner, where it may be used for fraudulent purposes, sold on the dark web, or employed in targeted advertising, all without the user’s knowledge or consent. This poses a significant threat to privacy and security.
4. Data Transmission
Spyware is designed to covertly infiltrate devices and silently monitor and collect a user’s personal and sensitive information, including keystrokes, browsing habits, and login credentials. Once the data is collected, it is transmitted to a remote server controlled by the spyware operator, often through encrypted channels to avoid detection by network security measures. This ensures that the data is sent without raising alarms, allowing the spyware to remain undetected on the device and continue extracting data. The stealthy transmission of spyware not only poses a significant privacy threat by allowing attackers to exploit the data for identity theft, financial fraud, or sale on the dark web, but also makes the data vulnerable to interception if unencrypted communication is used.
5. Persistence
Spyware is malicious software that infiltrates devices to stealthily gather information without consent, using sophisticated persistence mechanisms to remain undetected. It embeds itself within the system, often altering registry keys or masquerading as legitimate files, and creates services that restart after reboots, ensuring its continuous operation. These tactics allow spyware to stay active, complicating its removal and requiring advanced tools for eradication. Its persistence poses a significant threat to user privacy, as it can monitor and transmit data persistently, highlighting the need for robust security measures and vigilant system monitoring to protect against such invasive software.
Causes of spyware
Spyware infiltrates devices through various deceptive means, often exploiting user behavior and software vulnerabilities. Common methods include phishing attacks, bundling with legitimate software, and exploiting system or application flaws. Understanding these causes is crucial for preventing unwanted spyware installation and protecting personal and organizational data.

1. Misleading marketing
Misleading marketing is a common method for spreading spyware, where seemingly helpful software, such as hard disk cleaners or download managers, is infused with spyware and promoted with exaggerated features. These deceptive promotions can be found on both lesser-known and reputable download websites, often packaged with legitimate applications to hide their malicious intentions. Once installed, the spyware secretly collects personal information, resulting in privacy breaches and security risks such as identity theft and targeted phishing. Users should carefully assess software origins and marketing assertions to safeguard themselves against these hidden infiltrations that take advantage of their trust and lack of technical knowledge.
2. Phishing or spoofing
Phishing and spoofing are primary methods used by cybercriminals to spread spyware, taking advantage of human trust to bypass security measures. Phishing tricks users into providing sensitive information through emails or websites that appear legitimate, while spoofing involves pretending to be a trusted source to deceive individuals into compromising their online safety. These tactics are successful because they exploit the user’s trust, often leading to the unintentional installation of spyware that secretly collects personal data. The consequences of such breaches can include identity theft, financial loss, and serious violations of privacy. Awareness and understanding of these deceptive techniques are crucial for improving protection against the hidden dangers of spyware.
3. Security vulnerabilities
Spyware capitalizes on security vulnerabilities in software and operating systems, exploiting outdated or unpatched systems, weak passwords, and poorly designed applications lacking in robust security measures. Attackers deploy a variety of tactics, including phishing emails, malicious websites, and deceptive software downloads, to surreptitiously install spyware and gain unauthorized access to personal information. This can result in privacy invasions and financial losses. To safeguard against these threats, it is essential to consistently update software, enforce strong cybersecurity practices, and educate users on the dangers of engaging with suspicious emails and links, thereby strengthening defenses against such covert operations.
4. Software bundles
Software bundles are a common method for spyware to infiltrate systems by taking advantage of the appeal of free or discounted software to attract users. These bundles often include unnecessary programs, such as covert spyware, along with a desired application. Users may unintentionally agree to install the entire bundle during the installation process due to misleading messages and unclear terms of service, resulting in the stealthy installation of spyware on their system. Once installed, the spyware can monitor user activity, collect personal information, and decrease system performance. This deceptive distribution strategy relies on user negligence and the concealment of the bundle’s contents, highlighting the importance of carefully reviewing software installations to prevent falling victim to such deceitful practices.
5. Trojans
Trojans, named after the deceptive wooden horse in ancient Greek mythology, present a significant threat to digital privacy and system security by acting as a gateway for spyware. These malicious entities masquerade as harmless software to deceive users into installation. Once activated, they compromise systems by creating backdoors that cybercriminals can exploit to secretly install spyware, which can capture personal information such as keystrokes, browsing habits, and sensitive data. The danger of Trojans is heightened by their ability to bypass security measures, taking advantage of users’ trust and serving as an effective method for spreading spyware. Recognizing the deceptive nature of Trojans is crucial for protecting against the covert infiltration of spyware into our digital lives.
Common Symptoms of Spyware Infection
In the current digital era, spyware infections have become a prevalent concern for computer users. These malicious programs can surreptitiously infiltrate your system, compromising your privacy and impeding your device’s performance. The following are the most common symptoms that may indicate your computer has been affected by a spyware infection.
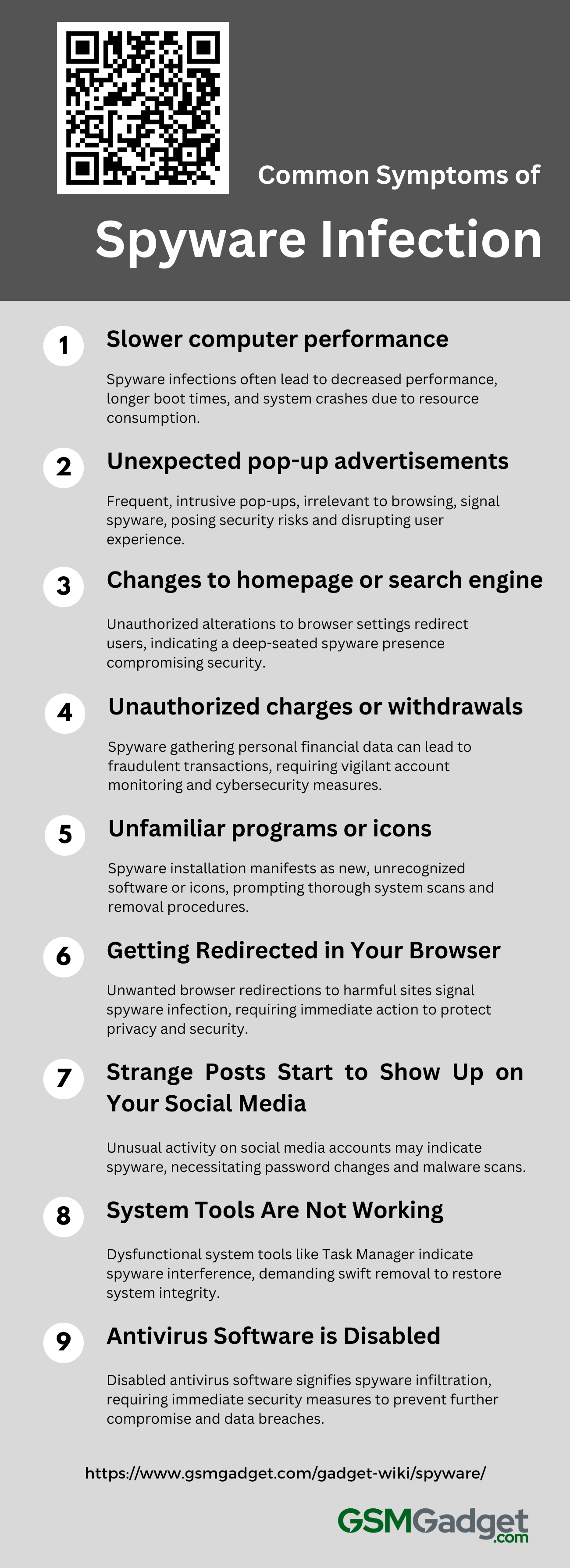
1. Slower computer performance
A spyware infection often results in a significant decrease in computer performance, characterized by longer boot times, delayed responses, and overall slowness in tasks that were previously efficient. Spyware operates stealthily in the background, consuming significant CPU and memory resources, leading to performance bottlenecks and frequent system crashes. Users may also observe increased hard drive activity and slower internet speeds, as the spyware continuously accesses and transfers data. These symptoms not only impact productivity but also indicate potential security risks, underscoring the importance of conducting a thorough scan and cleanup using trusted anti-malware software.
2. Unexpected pop-up advertisements
A common symptom of spyware infection is the frequent and unexpected emergence of pop-up advertisements, which are not only intrusive but may also appear randomly, disrupting the user experience and posing the risk of redirecting to malicious websites. These pop-ups often bear no relation to the user’s current browsing activity and may present suspicious or irrelevant products and services, sometimes even imitating legitimate system alerts. Their presence is a red flag, indicating that spyware may have covertly installed itself on the system to manipulate web traffic for ad revenue or to spread further malware, all without the user’s consent. Such ads can slow down the device and, if interacted with, escalate to more serious security compromises.
3. Changes to homepage or search engine
A prevalent symptom of spyware infection is the unauthorized change of internet browser settings, such as the homepage or default search engine, to redirect users to potentially harmful websites that may compromise their security or collect personal information. These persistent alterations resist user efforts to restore original settings, with the browser reverting to unfamiliar pages, indicating a more profound system vulnerability. Such disruptions not only affect the user experience but also pose significant privacy and security risks, often benefiting attackers through ad revenue or data collection. Persistent changes despite attempts to correct them suggest a deep-rooted spyware presence that necessitates prompt action to safeguard privacy and system integrity.
4. Unauthorized charges or withdrawals
One of the most concerning indicators of a spyware infection is the occurrence of unauthorized charges or withdrawals on your financial accounts. This harmful software covertly gathers personal information, such as credit card and bank account numbers, as well as online passwords. If hackers obtain this confidential data, they can carry out fraudulent transactions, leading to financial losses. Frequently, individuals only realize the breach when they notice unfamiliar transactions on their statements or receive alerts for purchases they did not authorize. To avoid such security breaches, it is crucial to diligently monitor your account activities and implement robust cybersecurity measures.
5. Unfamiliar programs or icons
A common symptom of spyware infection is the unexpected appearance of unfamiliar programs or icons on your device, often without any direct action from you. This can signal that spyware, which is designed to stealthily monitor and transmit your personal information, has been installed on your system. You may notice new toolbars in your web browser, unexpected icons on your desktop, or unrecognized programs in your system’s application directories. These signs are serious indicators of privacy and security breaches, prompting the need for a comprehensive system check. To address such issues, it is crucial to use reputable anti-spyware tools to scan for and eliminate these covert threats.
6. Getting Redirected in Your Browser
Experiencing unexpected browser redirections is a common symptom of spyware infection. When attempting to navigate to a chosen website, users may be involuntarily redirected to a different, potentially harmful site. These redirects can lead to ad-laden pages or phishing sites designed to harvest personal information. Additional signs of a compromised system include persistent pop-up ads, changes to the homepage, and unapproved new toolbars and extensions. These intrusions pose a threat to privacy and security, often requiring the use of a trusted anti-spyware tool to address the issue. Recognizing these symptoms is crucial for maintaining the integrity of one’s online experience and safeguarding digital information.
7. Strange Posts Start to Show Up on Your Social Media
Unusual activity on your social media accounts, such as posts, comments, or messages you don’t recognize, can be a telltale sign of spyware infection. This malicious software covertly breaches your device to access and manipulate your digital profiles, often aiming to steal data or disrupt your online standing. The content posted by spyware can vary from seemingly harmless ads to offensive material, posing a threat to your reputation and relationships. It’s essential to act swiftly by changing passwords, scrutinizing app permissions, and conducting an anti-malware scan to eliminate the spyware and protect your digital identity from further unauthorized actions.
8. System Tools Are Not Working
A spyware infection can be identified by the dysfunction of essential system tools such as Task Manager, Registry Editor, System Restore, or Activity Monitor. These utilities may become unresponsive, fail to launch, or close unexpectedly, often displaying error messages or having their options grayed out due to spyware’s interference to evade detection and removal. Spyware may also tamper with the tools’ functionality, presenting false information or inaccurately reporting system resources to conceal background activities. Such disruptions are serious indicators of compromised system integrity, undermining both security and performance, and necessitate swift action to remove the spyware and safeguard the system and sensitive data.
9. Antivirus Software is Disabled
A telltale sign of spyware infection is the unexpected disabling or malfunctioning of antivirus software, leaving the system defenseless and masking the malware’s presence. This deactivation can prevent updates and scans, hindering problem diagnosis and resolution. Spyware, aiming to collect sensitive data and execute unauthorized tasks, may also slow down the system, trigger unexplained network activity, and cause the emergence of intrusive ads or toolbars. Such symptoms necessitate immediate security audits and corrective action. Users should be vigilant, practice safe downloading, and employ reliable security tools to protect against further incursions and potential data breaches.
The Risks of Spyware
Spyware presents a substantial threat to both personal privacy and corporate security by covertly infiltrating systems to monitor user activity and steal sensitive data. As technology advances, so do the strategies of spyware developers, making it more difficult to identify and address these risks. Recognizing the different types of spyware and their potential consequences is essential for maintaining strong cybersecurity defenses.

1. Privacy invasion
In the digital age, spyware presents a significant threat to privacy by surreptitiously collecting sensitive information from devices without authorization. It utilizes deceptive tactics such as downloads, email attachments, and compromised websites to monitor user behavior, record keystrokes, and obtain private data such as login credentials and financial information. The repercussions of such breaches are serious, including identity theft, financial scams, corporate espionage, and major security breaches. As spyware becomes more advanced and can evade traditional antivirus software, it is essential for individuals and organizations to implement advanced security measures and remain vigilant in their online activities to prevent these covert intrusions. The use of spyware by cybercriminals and occasionally government entities underscores the critical need for enhanced cybersecurity measures and awareness to combat these threats.
2. Identity theft
Spyware, a type of malware, poses a significant risk to personal identity security by infiltrating computing devices to monitor and collect sensitive data such as keystrokes, browsing habits, and financial information. This unauthorized access can lead to identity theft, resulting in consequences like financial loss, unauthorized transactions, and damage to one’s credit score and reputation. To combat these risks, it is important to use updated anti-spyware tools, practice cautious online behavior, create strong, unique passwords, and regularly monitor financial transactions to protect against such intrusions and safeguard one’s digital identity.
3. Financial loss
The stealthy nature of spyware poses a significant threat to financial security, as it can surreptitiously infiltrate devices to collect sensitive financial information, such as credit card details, bank account numbers, and online banking credentials. By recording keystrokes and intercepting communications, spyware allows cybercriminals to carry out unauthorized transactions, resulting in identity theft, depleted bank accounts, and fraudulent charges. The impact on both individuals and businesses can be severe, with victims facing the arduous process of credit restoration and companies experiencing the loss of confidential trade secrets or strategic information due to corporate espionage. To mitigate these risks, it is essential to implement strong cybersecurity measures, such as utilizing reputable anti-spyware tools, conducting routine system evaluations, and educating users to safeguard personal and organizational finances against the covert threats of spyware.
4. Legal consequences
The use of spyware, which is malicious software that secretly collects sensitive data, poses significant legal risks with severe consequences for both individuals and organizations. Unauthorized surveillance or data interception carried out by spyware violates privacy and data protection laws, such as the GDPR, and can lead to criminal charges, hefty fines, or imprisonment. Companies that use spyware to monitor employees or competitors face legal repercussions, damage to their reputation, and loss of consumer trust. Furthermore, activities related to spyware, such as keystroke logging for stealing passwords and financial information, constitute identity theft and breach computer access laws. It is crucial to understand that any short-term advantages of spyware are far outweighed by the long-term legal implications, highlighting the importance of adhering to ethical standards and legal regulations in the technology sector.
5. Corporate espionage
In the competitive landscape of business, spyware is a malicious tool used for corporate espionage that poses a threat to the security of proprietary information and the integrity of company operations. These covert programs have the ability to infiltrate networks and secretly gather and transmit sensitive data such as trade secrets, financial records, and intellectual property to unauthorized parties, potentially resulting in financial losses and harm to a company’s reputation. The increasing complexity of spyware, including tactics like keyloggers, info stealers, and Trojans, highlights the need for businesses to implement comprehensive cybersecurity measures. These measures should encompass regular network assessments, the deployment of advanced anti-spyware technologies, and thorough training programs to educate employees on security best practices. Taking proactive steps is crucial in safeguarding against the hidden threats of spyware and preserving a company’s competitive edge in the market.
Protecting Yourself against Spyware
Protecting oneself against spyware requires a combination of practicing good digital habits and utilizing security software. Here are some essential steps that can be taken:
- Install reputable antivirus and anti-spyware software: Ensure that it is kept current and conduct routine scans.
- Keep your operating system and software updated: Ensure that it is kept up-to-date and perform regular scans.
- Be cautious with downloads and attachments: Download files only from trusted sources and exercise caution when opening email attachments, even if they are from familiar contacts.
- Use strong, unique passwords: Consider utilizing a password manager to effectively manage and store your passwords.
- Enable a firewall: Most operating systems are equipped with a built-in firewall that can assist in blocking malicious traffic.
- Be careful with links and websites: Do not click on suspicious links or visit questionable websites.
- Educate yourself about phishing scams: Learn how to identify and prevent phishing attacks.
- Limit sharing of personal information: Be cautious of the information you disclose online and to whom you disclose it.
- Use secure networks: Avoid using public Wi-Fi for sensitive transactions, or utilize a VPN to encrypt your connection.
