A phishing attack is a form of cybercrime where attackers deceive individuals into revealing sensitive information, such as login credentials, credit card numbers, or other personal data, by masquerading as a trustworthy entity in digital communication. Typically executed through email, these attacks can also occur via text messages, phone calls, or malicious websites. Attackers craft convincing messages or set up fake websites that closely mimic those of legitimate organizations, prompting victims to enter their information or download malware. The goal of phishing is to fraudulently obtain valuable information for malicious purposes, such as identity theft, financial gain, or unauthorized access to secure systems.
How Phishing Attacks Work

1. Preparation
The first stage of a phishing attack involves meticulous preparation by the attackers. They select their target—be it an individual or an organization—and gather as much information as possible to make their attack convincing. This might involve researching the target’s use of financial services, their social media activity, or any recent interactions with tech support or customer service. Attackers often use tools like email address finders or social engineering techniques to collect email addresses and personal information. The goal is to craft a phishing message that is tailored to the target’s expectations and habits, increasing the likelihood of the deception being successful. This preparation phase is critical because the more personalized and believable the phishing attempt is, the higher the chances of the target falling for the scam.
2. Distribution
Once the attackers have prepared their phishing campaign, the next step is distribution. This involves sending out the phishing messages to the intended targets. The distribution method can vary depending on the type of phishing attack. For email phishing, attackers use spoofed email addresses to send out emails that appear to come from legitimate sources. In the case of smishing (SMS phishing), messages are sent via text. Vishing (voice phishing) involves phone calls to the targets. Attackers may also use social media platforms or compromised websites to distribute phishing links. The distribution phase is designed to reach as many targets as possible in the hope that even a small percentage will respond to the fraudulent communication.
3. Deception
Deception is the core of a phishing attack. In this phase, attackers use various tactics to trick the target into believing that the phishing communication is legitimate. This could involve creating fake websites that mimic real ones, sending emails that appear to come from a trusted source, or using urgent language that prompts immediate action. The deception often exploits the target’s trust in familiar brands or institutions, such as banks, tech companies, or government agencies. Attackers may claim that the target’s account has been compromised, that they need to verify their identity, or that they are eligible for a refund or prize. The aim is to create a sense of urgency or fear, prompting the target to act without thinking critically about the authenticity of the request.
4. Collection
The collection phase is where the attackers harvest the information or assets they tricked the target into giving. This could involve the target entering sensitive information—such as login credentials, financial information, or personal identification numbers—into a fake website. In other cases, the target might download malware that gives the attacker access to their device and data. The collected information can be used for various malicious purposes, including identity theft, unauthorized financial transactions, or further phishing attacks. The success of the collection phase depends on the effectiveness of the deception phase; the more convincing the scam, the more likely the target is to provide the desired information or access.
5. Exploitation
In the final phase of a phishing attack, the attackers exploit the information or access they have obtained. This could involve selling stolen data on the dark web, using financial information to make unauthorized purchases, or accessing the target’s network to launch further attacks. The exploitation phase can have devastating consequences for the target, including financial loss, identity theft, and compromised security. In some cases, the attackers may hold the stolen data for ransom, demanding payment from the target to prevent its release. The exploitation phase underscores the importance of cybersecurity measures and vigilance in recognizing and avoiding phishing attempts, as the impact of a successful phishing attack can be far-reaching and long-lasting.
Types of phishing attacks
Phishing attacks exploit various communication channels, including email, phone calls, and text messages, to execute schemes like stealing login credentials or financial data. Understanding the different types of phishing attacks, such as email phishing, spear phishing, and vishing, is crucial for enhancing cybersecurity measures and protecting personal and organizational data.
- Bulk phishing emails (DND)
- Spear phishing attacks
- Whaling attacks
- Clone phishing attacks
- Evil twin attacks
- Voice phishing
- SMS phishing
- Page hijack attacks
- Email phishing
- Smishing and Vishing
- Angler Phishing
Signs of a Phishing Attack

1. Suspicious Email Senders
Phishing attacks often begin with emails that appear to come from reputable sources but are actually from fraudulent senders. These emails might mimic the format of legitimate communications from well-known companies but come from email addresses that have subtle discrepancies, such as misspellings or additional characters. For example, an email claiming to be from a legitimate bank might come from an address like “support@bankofarnerica.com” instead of “support@bankofamerica.com”.
2. Requests for Personal Information, Credentials
A common tactic in phishing emails is the request for personal information or credentials. Legitimate organizations typically do not ask for sensitive information like passwords, social security numbers, or bank account details via email. Phishing attempts may direct you to a form or website where you are asked to enter this information, often under the guise of verifying your identity or updating your account.
3. Urgency or Threatening Language
Phishing emails frequently use urgent or threatening language to create a sense of panic or urgency, compelling the recipient to act quickly. This tactic is designed to prevent the recipient from thinking critically about the email’s authenticity. Common phrases may include warnings that an account will be closed, a service will be suspended, or a deadline is imminent unless immediate action is taken.
4. Linguistic Errors
Many phishing emails contain linguistic errors that can be a red flag. These might include awkward phrasing, incorrect grammar, or unusual word choices, which are not typically seen in professional communications from legitimate organizations. These errors can result from the email being translated from another language or the sender not being fluent in the language used.
5. Inconsistencies in Web Addresses
Phishing emails often include links that appear legitimate but direct you to fraudulent websites. These URLs may have misspellings or use a misleading domain name that mimics a genuine site. For instance, a phishing link might use “www.bankofarnerica.com” instead of “www.bankofamerica.com”. Always hover over links to see the actual URL before clicking.
6. Unusual Requests
Phishers may make unusual requests that are out of the ordinary for the supposed sender. For example, you might receive an email from your company’s CEO asking you to wire money urgently or provide access to confidential files. These requests typically create scenarios that seem plausible but are designed to trick you into performing actions that compromise security.
7. Mismatched Email Addresses, Links, and Domain Names
A key indicator of phishing is mismatched or spoofed email addresses, links, and domain names. The display name might look correct, but the actual email address or link URL could be different. It’s important to check the sender’s email address and any links included in the email carefully for any discrepancies that suggest phishing.
8. Poor Spelling and Grammar
Phishing emails often contain poor spelling and grammar, which can be a telltale sign of a scam. While minor typos can occur in legitimate emails, frequent and glaring mistakes are common in phishing attempts because the emails may be crafted by non-native speakers or generated in haste.
9. Attachments or Links
Attachments or links in emails can be vehicles for malware or direct you to phishing sites. Unsolicited emails that encourage you to download an attachment or click on a link should be treated with suspicion. These attachments can contain malware that can infect your device, and links might redirect you to a site designed to steal your personal information.
Consequences of Falling Victim to Phishing Attack

1. Data Theft
Data theft is a primary consequence of falling victim to a phishing attack. Cybercriminals use phishing to trick individuals into divulging sensitive information, such as personal identifiable information (PII), financial data, intellectual property, and trade secrets. Once this data is stolen, it can be sold on the dark web, used for competitive advantage, or employed in further cybercrimes. The loss of such critical information not only jeopardizes the privacy and security of individuals but also poses significant risks to the operational integrity and competitive standing of businesses.
2. Financial Loss
Financial loss is a direct and immediate consequence of phishing attacks. Victims may find unauthorized transactions, drained bank accounts, or fraudulent charges on their credit cards. For businesses, the financial impact extends beyond the immediate theft of funds to include customer churn, legal fees, and the cost of remediation efforts to secure breached systems. The Ponemon Institute’s research highlighted that successful phishing attacks now pull in millions per attack, underscoring the substantial financial risk phishing poses to organizations and individuals alike.
3. Identity Theft
Identity theft occurs when attackers use stolen personal information, obtained through phishing, to impersonate victims. This can lead to unauthorized opening of credit accounts, filing of fraudulent tax returns, or even medical fraud. The repercussions for victims can be long-lasting, affecting their credit scores, financial stability, and personal reputation. Recovering from identity theft often requires significant time and resources, making it one of the most distressing outcomes of falling prey to phishing schemes.
4. Compromised Security
Phishing attacks compromise the security of individuals and organizations by installing malware or gaining unauthorized access to networks. This can lead to a broader infiltration, where attackers can steal more data, plant ransomware, or create backdoors for future access. The compromised security can disrupt operations, lead to data breaches, and significantly weaken the cybersecurity posture of the affected entity. Maintaining robust security measures and educating users on recognizing phishing attempts are critical in mitigating this risk.
5. Loss of Trust
Victims of phishing attacks, especially businesses, suffer a significant loss of trust among customers, partners, and stakeholders. The revelation of a data breach can tarnish a company’s reputation, leading to a decline in customer loyalty and potentially long-term damage to the brand. Rebuilding trust requires transparent communication, remediation efforts, and enhanced security measures to prevent future incidents. The impact on trust underscores the importance of proactive cybersecurity practices.
6. Regulatory Penalties
Falling victim to a phishing attack can result in regulatory penalties for businesses, especially if the breach involves sensitive customer data. Regulations such as GDPR, HIPAA, and others mandate strict data protection measures and impose hefty fines for non-compliance. The legal and financial repercussions of failing to protect data underscore the necessity for organizations to adhere to cybersecurity best practices and regulatory requirements to avoid such penalties.
7. Operational Disruption
Operational disruption is a common aftermath of phishing attacks. Businesses may need to shut down systems to contain the breach, leading to downtime, lost productivity, and interrupted services. The process of investigating the attack, restoring systems, and implementing stronger security measures can be time-consuming and costly. This disruption not only affects the bottom line but also strains resources and can have a lasting impact on the operational efficiency of the affected organization.
Preventing Phishing Attacks
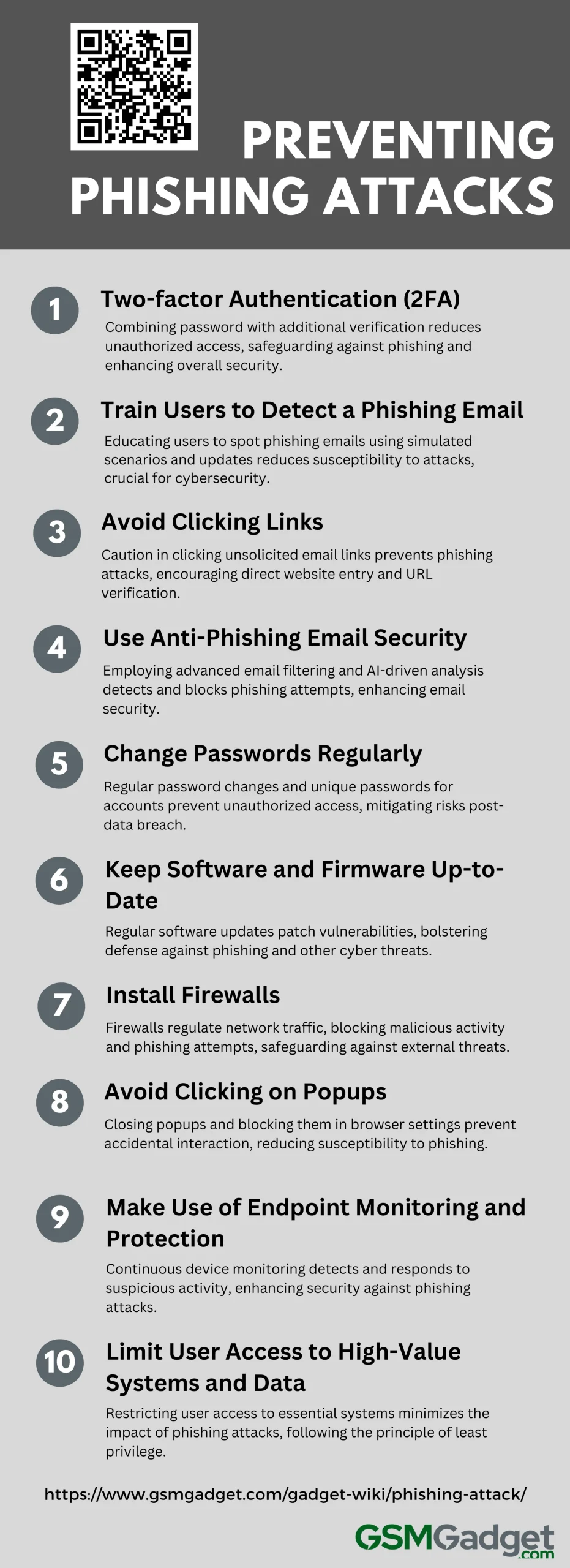
1. Two-factor Authentication (2FA)
Two-factor authentication (2FA) significantly enhances security by requiring two forms of identification before access is granted. This method is highly effective in preventing unauthorized access, even if a password is compromised. 2FA combines something you know (like a password) with something you have (such as a mobile device for a one-time passcode) or something you are (like a fingerprint). This added layer of security makes it much harder for attackers to gain unauthorized access, protecting against various cyber threats including phishing attacks.
2. Train Users to Detect a Phishing Email
Training users to recognize phishing emails is crucial in preventing phishing attacks. Effective training should include identifying suspicious email characteristics such as urgent language, misspellings, or unfamiliar sender addresses. Interactive methods like simulated phishing scenarios can enhance user awareness and reduce susceptibility to real attacks. Regular updates on new phishing techniques and maintaining an informed user base are essential components of a robust cybersecurity strategy.
3. Avoid Clicking Links
One of the simplest yet most effective ways to prevent phishing attacks is to avoid clicking on links in unsolicited emails or messages. Users should be trained to hover over links to verify their destination before clicking and to recognize signs of malicious URLs. Encouraging the practice of entering website addresses directly into the browser rather than clicking on links can also significantly reduce the risk of falling victim to phishing scams.
4. Use Anti-Phishing Email Security
Implementing anti-phishing email security measures can drastically reduce the incidence of phishing attacks. These measures include using advanced email filtering solutions that can detect and block phishing attempts before they reach the user. Technologies such as AI-driven threat intelligence and real-time link analysis can identify and quarantine suspicious emails, thus protecting users from potential threats.
5. Change Passwords Regularly
Regularly changing passwords is a fundamental security practice that can prevent unauthorized access following a data breach. It is recommended to change passwords every three months and immediately after learning of a potential security incident. Using strong, unique passwords for different accounts can also prevent attackers from gaining access to multiple services if one password is compromised.
6. Keep Software and Firmware Up-to-Date
Keeping all software and firmware up-to-date is critical in protecting against phishing and other cyber threats. Software updates often include patches for security vulnerabilities that could be exploited by attackers. Ensuring that all systems and applications are regularly updated minimizes the risk of security breaches and enhances overall system integrity.
7. Install Firewalls
Firewalls act as a barrier between trusted internal networks and untrusted external networks, such as the internet. They monitor and control incoming and outgoing network traffic based on predetermined security rules. Installing and properly configuring firewalls can effectively block malicious traffic and prevent phishing attacks by limiting the exposure of sensitive systems to potential threats.
8. Avoid Clicking on Popups
Popups can be a tool for phishing attacks, often designed to mimic legitimate requests for information. Users should be instructed to close popups without interacting with them and to adjust browser settings to block popups by default. This reduces the risk of accidentally clicking on a malicious link and provides an additional layer of protection against phishing.
9. Make Use of Endpoint Monitoring and Protection
Endpoint monitoring and protection involve the use of software tools to continuously observe and manage devices accessing the network. These tools can detect and respond to unusual activities that may indicate a phishing attack in progress. Implementing endpoint protection provides visibility into potential security threats and allows for immediate response to mitigate risks.
10. Limit User Access to High-Value Systems and Data
Limiting user access to essential systems and data is a key security measure. By implementing the principle of least privilege, users are granted access only to the resources necessary for their job functions. This minimizes the potential impact of a phishing attack, as attackers gaining access through a compromised account are restricted in what they can reach and exploit.
